Desktop application security in C# - High Tech Institute - application security course, application security training, application security workshop
Comparing Netsparker Cloud-based and Desktop-based Security Software solutions – Which solution is best for you?
Finest approaches to secure your web application | Metricoid - A Custom Software Product Development & Consulting Company
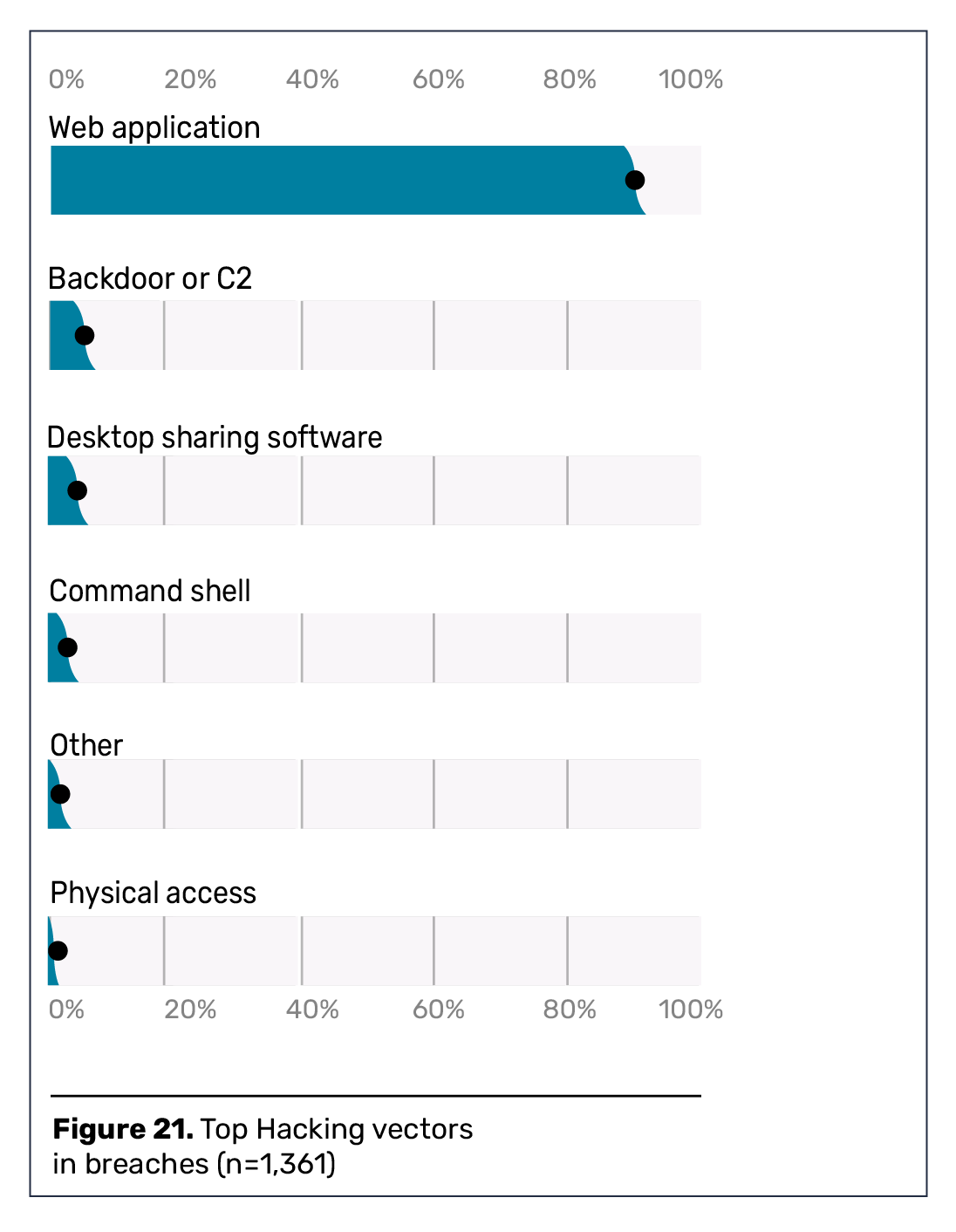
www-project-desktop-app-security-top-10/index.md at main · OWASP/www-project-desktop-app-security-top-10 · GitHub

Application Security Program Handbook eBook by Derek Fisher | Official Publisher Page | Simon & Schuster UK

First Application Security Testing Solution to Analyse Open Source and Proprietary Code on the Developer's Desktop - IT Security Guru